iPhones are launched less chaotically unlike Android devices that are launching left and right every week. Apple is obsessed with privacy and security, apart from the mind-blowing cameras. You won’t see most of the Android smartphone brands pushing their ads, tagging them as ‘privacy-focused’ but that’s not for iPhone. Let’s see what makes iPhones more secure than others. P.S. Your perception towards iPhones may change reading this blog post so “read with care”.
How is iPhone The Most Secure Smartphone
1. Tighter Control Over Hardware and Software

When you buy an Android smartphone, you are buying a device whose components were supplied by different companies. The software is supplied by Google plus the OEM’s customizations on it. There are countless components including ISP, haptic feedback, and all kinds of different ICs that are integrated.
Apple keeps tighter control over the hardware and only sources it from authorized manufacturers. While this can still lead to complications, Apple has slowly started to manufacture in-house hardware as much as it can, and the recent shift to M-series chipsets is an example of this. iOS is a homegrown operating system optimized to work with all hardware and other components onboard. Apple keeps chip-level controls allowing it to manage everything at the atomic level. It basically gives Apple a strong defence against any hardware or software exploit making any attempts to strike the device obsolete.
The tighter control serves different functions. Unlike Android which is a puzzle, all the Apple hardware, software, and services are capable of working in an ecosystem like a well-oiled machine.
Also Read: How To Check iPhone Warranty In 2 Minutes?
2. A Patch Goes Through All
On the Android front, there are too many players including Google, the OEMs, and the carriers among others who are responsible to gather information on the vulnerabilities, threats, or bugs and mobilize the patch. Even if we are talking about Google’s security patch, it is not now that Google has started providing it as a part of the Play Store that ensures it reaches users in time.
Apple doesn’t simply distribute iOS updates for years but also keeps their devices updated with patches to previously discovered vulnerabilities even if you check a device 5 years after its release. Moreover, these patches are released for almost all iPhone models meaning it reaches every user at the same time. For perspective, Android has a fragmentation issue where a phone eligible for an Android update may still wait for months to receive the update since it isn’t usually a ‘push to all’ kind.
3. Fortified Marketplace

Ideally, an app developer submits their app to Google for approval which goes under security implementation and malware checks, etc. Google does conduct all the checks to prevent malware-riddled apps and yet, iOS takes it a step further. The Cupertino-based giant already has stringent policies on apps uploaded on the marketplace. It requires all the developers to abide by the same or end up getting rejected.

The strict vetting process prevents malware and other ill-riddled apps from being submitted to the App Store and ultimately to the users who will end up downloading them.
Also Read: 5 Best Methods To Hide Apps On Apple iPhone
4. A Small Target To Hit
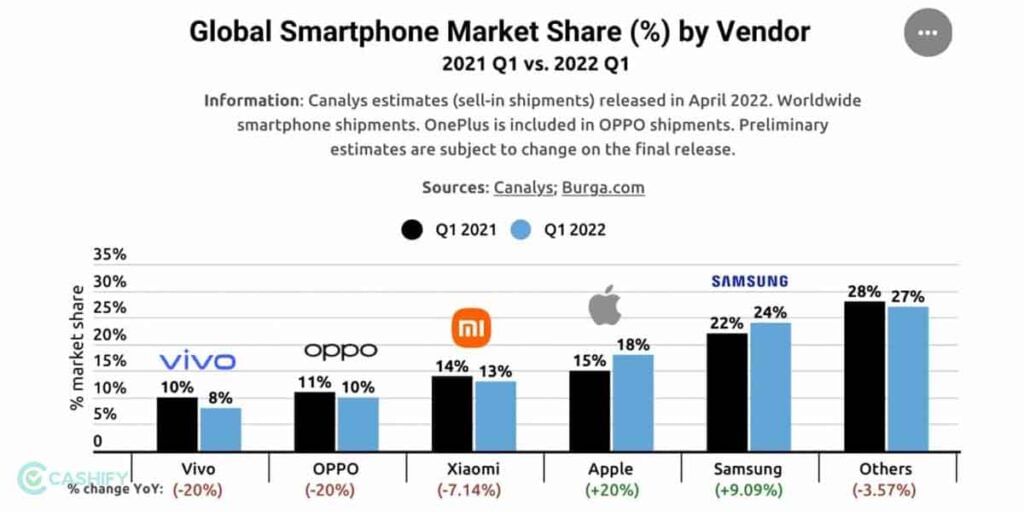
Keeping Apple’s defences against malware and intruders aside, iOS devices are a much smarter target for hackers. Android has a market share of around 71.8% worldwide while Apple’s share is 27.58%. When cyberattackers masquerade malicious codes as app downloads or clicks on links, Android ultimately becomes a larger target to hit and most importantly, its open-source nature expedites the process. Oftentimes, this reason is enough to explain why Android OS gets most cyberattacks while iOS receives minimal.
5. Sandboxing On The Go

Android OS is open source and thus, allows app developers to do a lot of customization, and seek out a lot of permissions running an app and whatnot. Counterintuitively, apps on iOS devices are designed differently to adhere to Apple’s policies. One of the major techniques that Apple uses when running apps is called sandboxing.
When you run an app on an iPhone, the system basically creates a walled-off space aka sandbox where the app runs and interacts with other apps, the OS, hardware, and services up to a certain threshold. In case the app in question contains malicious codes, the sandbox prevents it from infiltrating other apps and the OS thus, containing the damage.
6. Third-Party Apps Installation
On an Android device, you can simply download apps from the Play Store and there are manifold apps on it then in the App Store. You can even sideload apps from APK Mirror and other websites as it is completely free on Android. However, it also raises the security risk since you are basically downloading apps from unknown sources. You could be installing phishing apps, malware that is disguised as legit apps, and so on.
Turns out it is pretty difficult to sideload apps on iPhones. With the built-in security, Apple doesn’t allow third-party apps in the majority of cases. App Store is the single and largest source of legit apps that you can find but third-party apps are often out of reach. You can still install them by jailbreaking the iPhone which is the rooting equivalent of Android devices. Doing so isn’t easy as well which means you will certainly end up using the App Store as the sole source for apps anyways.
7. Secure Enclave For Biometrics

Apple has created an ecosystem within the SoC dubbed Secure Enclave. It is a write-only space that stores facial and fingerprint biometrics data in an encrypted manner. It doesn’t grant read access to any processes and thus, ensures the data is secured. Whenever a user provides their fingerprint or facial recognition, the information is passed through the Smart Enclave where the subsystem signals whether it is valid or not in a cryptographic manner. If and only if the stimuli are valid, the user is granted access.
Apart from that, facial recognition on iPhones is considered superior to any Android implementation. It cannot be spoofed using a 2D photo and a 3D face in most cases. Android devices are still playing catch up whereas Apple has leaped forward by upgrading its facial recognition tech.
Also Read: Guide On How To Connect iPhone To Laptop Really Fast: 3 Easy Ways
8. Gated Operating System
Compared to Android, iOS is still a pretty closed-source operating system, and for good reasons. It acts as a barrier for hackers from finding security flaws that they can exploit. Apple usually patches vulnerabilities it found in iOS almost immediately. Whereas Google takes time to cover the holes in its operating system. Although I would say Android is catching up, there’s still a long way for it to reach where Apple is concerned with its closed-source OS.
9. Sign-in With Apple
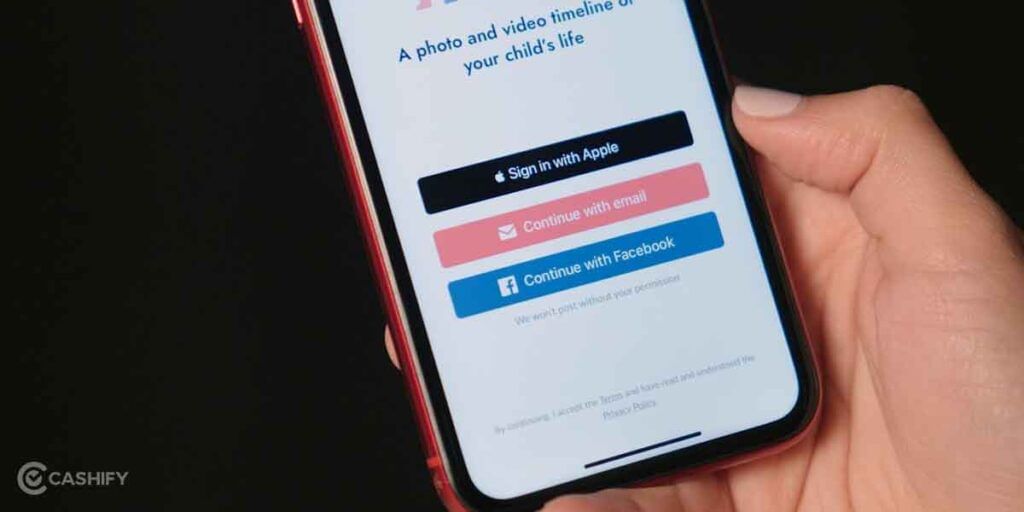
You will need to log in to an app or website to try it out or buy something, etc. When using social media sign-ins, you aren’t simply sharing the email address but the social media account as well. Not to forget the hassles of creating and remembering the new password you created for eternity. With that being said, Sign-in with Apple is a lot better way to bypass the aforementioned scenario.
When you use this feature or apps or websites, your Apple ID is shared while you can hide your actual email address. It creates a random email address that the websites capture where the emails are forwarded to your email address without leaving a trace. It essentially protects your email address while giving you a superfast way to sign in without being tracked on the web.
Also Read: Android Features On iPhone: 9 Features We Need On iOS!












































