Why are passwords not good enough? Before answering the question, what is two-factor authentication? Or What is dual authentication? Let us first understand why it is essential to improve your online security.
In today’s digital era, we constantly live our lives in and around smartphones and laptops. So much of our lives is happening on digital devices. That’s why our digital accounts have become the lead magnet for cybercriminals. So, if you want to add extra security to your user accounts, two-factor authentication (2FA) can help you.
However, what is two-factor authentication?
Does this question pop into your mind again and again?
Let us explain this to you in detail.
In simple terms, it is a security system in which users must verify themselves in two different ways to access a specific system, device, or application instead of just password authentication.
The first factor is your username and password; the second factor is something you might have as a unique – biometrics, security tokens, smartphone, etc.
This article explains dual authentication in detail and lists all its advantages, methods, importance, and best practices.
Also read: The State Of Cybersecurity: Threats, Solutions & Best Practices
Passwords are not Full-Proof But Still in use…

One can easily figure out your password, hack your system, print out the passwords, and hog more computer time. It means that there are much more secure alternatives than this. Still, usernames and passwords remain the most common form of user authentication.
The general rule of thumb is that you should keep the username strong enough so that no one can easily guess it. Of course, passwords are not foolproof, but it is better to use them for protection than not at all using any security measures. Here are a few reasons why passwords are not a foolproof solution.
- If you keep passwords like “12345678” or “000000”, they are easy to remember, and any hacker can easily track them in no time.
- You are required to remember too many passwords when you have too many online accounts. This habit leads to password recycling, and hackers can easily hack your account.
- Some users don’t give up and set hard passwords. So hackers cannot easily hack the account. However, if you give up and use a weak password for multiple accounts, there is a high chance of data breaches.
Here is where 2FA comes into the picture as a Rescue…
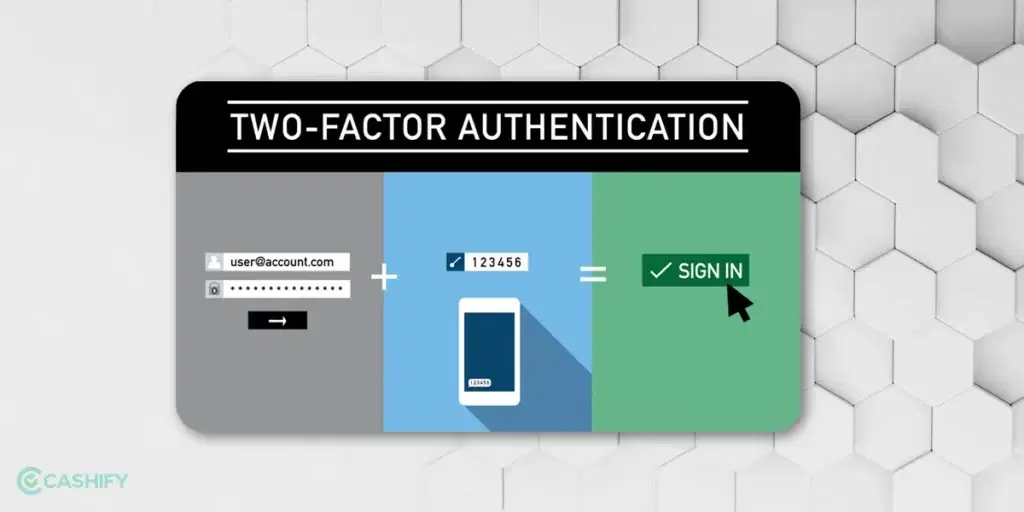
In simple terms, 2FA is an extra layer of security that helps you protect your personal information. 2FA ensures that a person trying to gain access to an online account is genuine. As a user, you need to undergo a two-step verification process.
- First, you need to enter the username and password. Once you enter it, you will not immediately get the access. You need to undergo the second step of verification.
- In the second factor, you can set one of the following factors.
- Knowledge Factor – PIN, Specific keystroke pattern, password, answers to secret questions
- Possession Factor – You can even set up a hardware token, smartphone, and credit card as two-factor authentication.
- Biometric Factor – Biometric pattern of your fingerprint, voice print, or an iris scan
Therefore, if your password gets stolen or your smartphone is lost, there is a low chance that someone could steal your second-factor information.
In the next section, we will understand the importance of dual authentication.
Also read: How To Reset Your Apple ID Password? A Complete Guide
Why 2FA is important?
Two-factor authentication might seem daunting. You need to follow the additional steps to access your digital devices. However, in today’s fast-paced digital era, cybercrimes are on top.
Cybercriminals easily target consumers’ sensitive information as traditional verification methods work no longer. Therefore, if you want cyber criminals not to steal your data and get access to your personal information, you should opt for two-factor authentication.
How does 2FA Work?
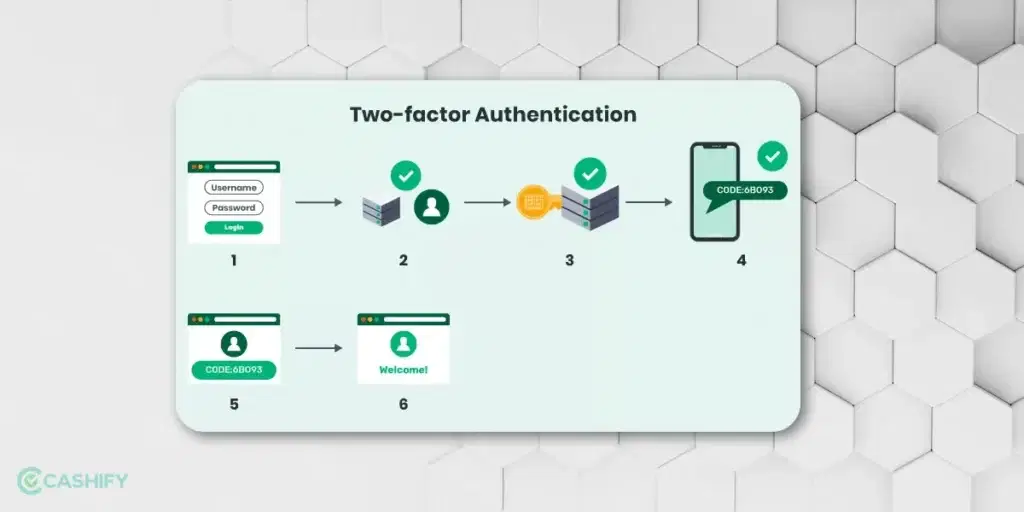
Here are some of the most common steps to enable 2FA, irrespective of application or vendor.
- First, you will get the prompt to log in by app or website
- After that, you need to log in to the app or the website by entering your username and password. The website or app’s server tries to find the match and identify you as a user.
- Now, the website or app prompts you to initiate the second step. In this step, you must provide biometrics, a smartphone, a security token, or an ID card.
- After that, you must enter the OTP generated during the previous step.
- Once you provide both factors, you will be authorised to access the website, app, or device.
Also read: Explained: What is Sim Swapping Attack? How To Stay Safe?
Types of 2FA Methods
If you are using any website or app that requires only a username and password for authentication and don’t use 2FA, there is a high chance that hackers will hack it eventually.
This does not mean that all two-factor authentication is the same. There are various types of 2FA; some are complex, and some are easy to implement. However, these 2FA offers better protection than passwords.
Here are a few common types of 2FA.
Hardware Tokens

It is one of the oldest forms of two-factor authentication. Hardware tokens are small and usually generate a new numeric code after each 30 seconds. Therefore, whenever users try to access the account, they need to enter the 2FA code into the website or app.
Nowadays, newer versions of hardware tokens are also available. Such tokens automatically transfer the two-factor authentication code whenever plugged into the PC’s USB port. Hackers can easily hack this type of 2FA.
SMS And Voice-based 2FA

SMS-based 2FA interacts directly with the user’s mobile device. Once the user enters the username and password, the website sends the unique OTP through text message. Users must enter the same OTP back into the website or app to get access.
The voice-based 2FA works the same way. In voice-based 2FA, users get the automatic call; in that call, they get the OTP verbally. Remember that this type of 2FA is good for low-risk activities, but for the website or app that stores your personal information, this type of 2FA is not recommended.
Software Tokens
It is one of the most popular and preferable 2FA types. In this type of 2FA, software-generated OTP is used.
- For that, you need to install the free 2FA app on your mobile or PC.
- After that, you must enter the username and password.
- Now, you will get the OTP; you need to enter the code in the app.
As the OTP is generated and displayed on a similar device, there is little to no chance of hacking.
Push Notifications

In this type of 2FA, users do not need to rely on 2FA code. Instead of it, websites and apps send push notifications to the user for authentication attempts.
As a device user, you can view the details and approve/deny access with a single tap. In simple terms, it is passwordless authentication, which requires no code or no extra interaction.
In push-notification 2FA, there is a direct connection between the retailer, the 2FA service, and the device. Therefore, there is no chance of phishing or unauthorised access. However, the only downside is that you need a reliable internet connection to access it.
Biometric Authentication
Biometric authentication treats the user as the token. It uses the user’s fingerprints, retina patterns, facial recognition, pulse, ambient noise, vocal points, etc are used as the 2FA. In today’s time, it is the most secure type of 2FA.
Now that you understand the different types of 2FA let’s briefly check out the pros of 2FA in the next section.
Also read: Cyber Swachhta Kendra: How To Keep Your Devices Bot Free?
Pros of two-factor authentication
- 2FA increases security by lowering the chance of hacking.
- Employees can access business information securely and remotely, improving productivity.
- When you use 2FA, you do not need to spend much on security management. It reduces the management cost.
- Using 2FA lets you do fraud prevention effectively.
- You can even integrate 2FA into your app as API integration. It will add an extra security level.
FAQs
Q. Which industries use two-factor authentication?
A. Almost every industry uses 2FA. However, retail, healthcare, media, travel, etc., mostly use two-factor authentication.
Q. Which threats can 2FA protect us from?
A. 2FA can protect us from major security threats like phishing, data breaches, stolen passwords, social engineering, etc.
Q. Is 2FA and MFA the same?
A. No. 2FA and MFA are not the same but are usually used interchangeably. 2FA is the subset of the MFA, and two authentication factors are used in it. However, in the MFA, more than two authentication factors are used.
Parting Words
Two-factor authentication is no longer a luxury but a necessity in 2024. Therefore, you should use it wherever it is possible. Also, remember, any of the above-discussed two-factor authentication is way better than not implementing none at all.
Generally, the first factor in 2-way authentication is the password, and the second factor is either text with a code or biometric using face, fingerprint, or retina. However, remember that 2FA improves security, but it is not foolproof.
Hopefully, reading this article answered your question – ‘What is two-factor authentication’? and its various methods, types, pros, cons, and importance. If you still have any queries, let us know in the comment section below.
Also read: How To File Cyber Crime Online In India?
Looking to upgrade to a better phone? We have a smart solution for you. Buy refurbished mobile phones at almost half price from Cashify. They come backed with a six-month warranty and 15-day replacement policy. Check out refurbished mobile phone sale now!